At present, the management and monitoring of confidential carriers and important confidential documents are getting more and more attention, such as: office laptops, USB flash drives, mobile hard drives, digital cameras, video cameras, voice recorders and confidential documents. The dense carrier and important confidential document management system adopts the traditional combination of barcode scanning and personnel access control, which has various drawbacks, which brings great inconvenience to the management of confidential carriers in enterprises and institutions. Due to the traditional bar code asset management method, real-time monitoring of important asset position changes cannot be realized. At the same time, the traditional access control system can only understand the entry and exit of personnel, and the personnel must actively present the access card, and cannot grasp the current location of the personnel in real time. Illegal personnel carry the secret carrier out of the manufacturing opportunity, making the confidential carrier and important documents leak.
RFID technology is used to realize the authority management and monitoring of the staff and visiting customers who enter and leave the confidential carrier, and to realize the monitoring of confidential carriers, prevention of loss management and inventory. The solution adopts active RFID reader and active RF card to realize remote recognition and monitoring function. The staff can realize access control attendance without active card swipe, and at the same time, the staff can set permissions (including regional authority, time limit, etc.). The use of sound and light alarms for the entry and exit of illegal personnel is proposed to avoid the loss of the confidential carrier.
Second, the system goal2.1, system requirements
Each company and organization has movable assets such as confidential and important documents, which can include: office laptops, USB flash drives, mobile hard drives, digital cameras, video cameras, voice recorders, confidential documents and important paper documents. Information, etc. In order to ensure the above-mentioned confidential carriers and important documents are effectively guaranteed, the requirements are as follows:
It is necessary to protect the important information stored in the laptop; to authenticate the person using the laptop; to effectively monitor the important paper documents and the data entry and exit areas; to carry out the removable electronic devices storing important information. Effective monitoring; effective monitoring of other confidential carriers.2.2, system goals
The security objectives of movable assets such as confidential and important documents are as follows:
The system automatically identifies the confidential carrier and displays the detailed information; the system automatically identifies the identification card of the person carrying the confidential carrier and records the detailed information; the system sets the authority for the personnel within the range of the entry and exit of the confidential carrier; the confidential carrier is not approved When brought out, the system automatically starts the sound and light alarm and records the detailed information; Third, the system structure and characteristicsThe confidential carrier and personnel access control system mainly manages and supervises the confidential carrier and important documents, and manages the personnel carrying the confidential carrier. The system consists of three parts: the confidential carrier management system, Personnel management system and back office management system.
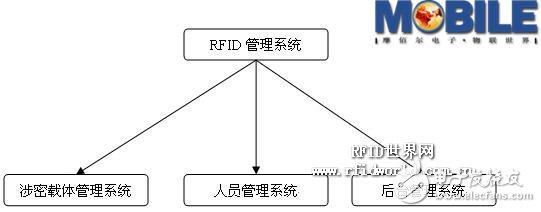
Figure 1 System composition diagram
3.1, confidential carrier management system
3.1.1 confidential carrier management function
This solution uses RFID technology to realize the intelligent management function of the confidential carrier, so the RFID tag needs to be deployed in key mobile assets (including confidential documents, laptops and others). According to the actual situation of the user and different categories of movable assets, the individuals that need to be identified are marked by electronic tags suitable for different media. Functional work steps
Attaching the confidential carrier and important documents to the active electronic tag; writing the information of the confidential carrier and the important file on the active electronic tag, the active electronic tag card number and the confidential carrier are in one-to-one correspondence; the active electronic tag and The information of the confidential carrier is uploaded to the central database of the management system: The system can only enter the control of the confidential carrier if it holds the certificate recognized by the system: Hold the certificate recognized by the system, and then handle the loan and return after entry; Search, check, carry, inventory Confidential carriers and important documents.3.1.2 confidential carrier prevention loss process
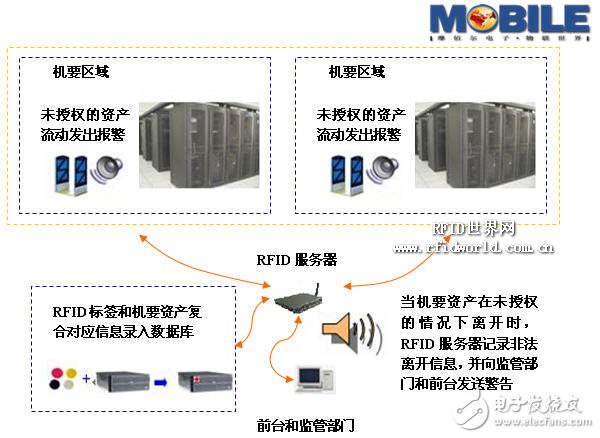
Figure 2. The confidential carrier prevention process
Using RFID technology to monitor and prevent loss management of dense carriers, not only can monitor the location and flow direction of each confidential carrier in real time, but also remotely monitor the number, name, outflow time, inflow time and carry of each confidential carrier. Information such as personnel information on the flow of confidential carriers.
The anti-loss management of the confidential carrier has the timeliness of the alarm when the loss occurs, so that the asset management department and the security personnel can handle the loss event in the shortest time after the loss occurs, and reach the lost site, thus eliminating the loss phenomenon;
When a person carries a regulated confidential carrier through the exit, the active reader/writer reads the ID number of both the person and the confidential carrier, and queries the server to find the confidential carrier. If the system does not get the authorization to leave, the system will start an audible and visual alarm, and the server sends the personnel and asset information represented by the two ID numbers to the asset management department and the security control room, and shows from which room the flow is made, so that the relevant Supervisors will arrive at the location of the confidential carrier where the alert occurred as soon as possible and further processing.
Flex Power Supply,Flex Power Supply 80Plus,700W Adapter Server Power Supply,Flex 700W Power Supply
Boluo Xurong Electronics Co., Ltd. , https://www.greenleaf-pc.com